Online scams: An overview + internet scams to avoid
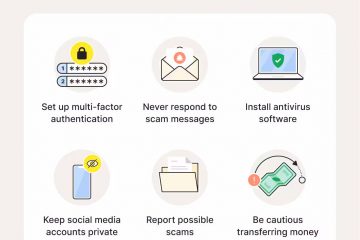
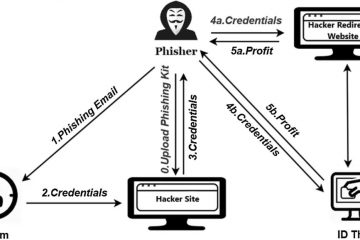
Reading Time: 9 minutesNew users lose billions to online scams every year, and many never recoup their losses. Read on to learn more about the most dangerous scams to watch out for in 2026. Then, find out how to help identify and avoid them by using a comprehensive online security tool with cutting-edge, AI-powered scam-detection features. The internet has created a fantastic means to explore new topics, stay connected with loved ones, shop, and even access healthcare. But Read more…